Hi everyone, creating a series of posts about SevOne NPM observability.
For those unfamiliar, SevOne is an NPM (Network Performance Management) solution, a network observability solution focused on providing visibility into which applications are consuming the network.
For those familiar with the VMware ecosystem, it is similar to vRNI (vRealize Network Insight), now called Aria Operations Network, however, I believe SevOne is a broader solution, providing “out-of-the-box” compatibility with other devices more easily, such as Cisco, Fortinet solutions, etc.
The objective of this series of posts will be to show how to configure SevOne to connect to devices in the vSphere environment. Another post will cover NSX and Fortinet SDWAN, followed by a more in-depth look at how to configure reports, network maps, etc.
Regarding integration, I’ll open a sidebar here.
There are two integration options we can explore. One uses the SNMP (Simple Network Management Protocol), in which we can monitor the devices in our environment for availability. For example, we can create reports and views of CPU and memory usage, as well as network interface utilization for a device, whether it’s a vSphere device or virtualized devices in the environment. Of course, we can also use physical devices (Cisco, Fortinet, etc.), It’s the same monitoring we could do using other SNMP-compatible solutions, such as Zabbix, Nagios, and Grafana, that is, an overview that allows us to identify failures in the network.
On the other hand, we can integrate with SevOne using protocols such as NetFlow, sFlow, IPFIX, etc. These protocols allow us to analyze network flows by inspecting packets passing through the network, giving us detailed insights into what’s traveling on the network—top flows by source or destination, for example, top countries accessed via the internet, which applications use the network the most, and what connects and communicates with what. Here lies the magic of the solution.
Think of yourself as a network manager. The company’s CIO walks into the room and asks, “What are our users accessing on the internet? Which applications are most accessed, and how can we prioritize them?” These are the kinds of questions that only a solution like this can answer. With SevOne, it’s possible to integrate a series of devices from different vendors to provide the most detailed view possible.
Integrating SevOne with vCenter and discovering devices:
I believe there are a few ways to do this, whether via manual insertion, discovery by network range, etc. I will try to approach the integration first via SNMP by configuring it manually, and then we will configure NetFlow to receive the traffic.
Configuring SNMP on vSphere:
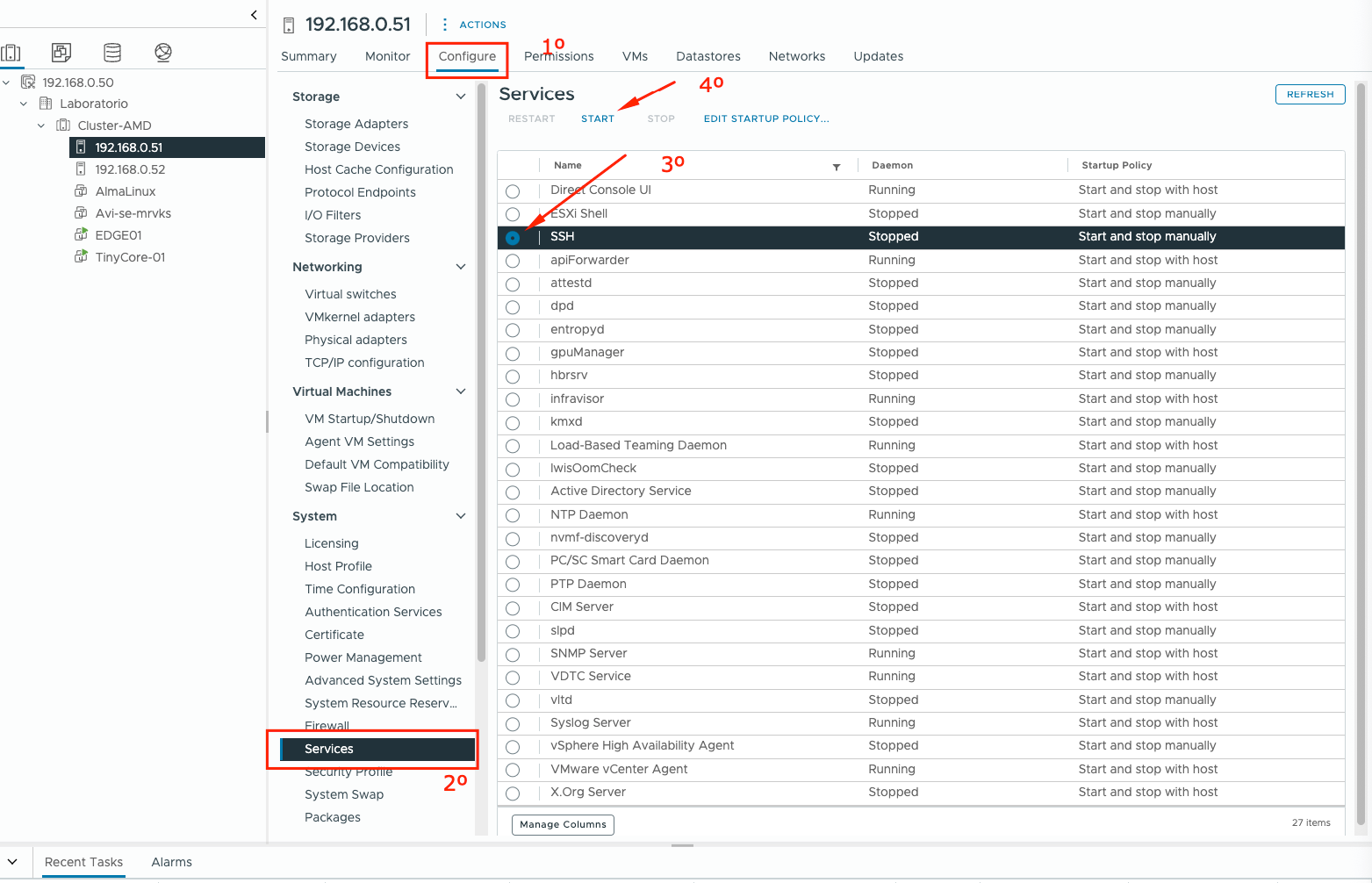
First, enable SSH on the hosts through vCenter by accessing the vCenter GUI interface > select the host > Configure > Services > SSH > Start, I am using vSphere 8, I believe that is the same process from vSphere 6.7 to 9.
After connecting through SSH into each host ESX’i, type:
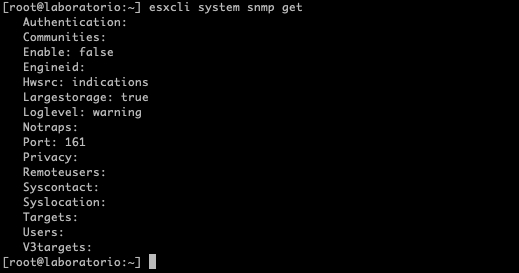
esxcli system snmp get
Most likely it will not have any information configured, as in the previous image, now type “esxcli system snmp set” to configure the target and community, in this case of course the target is SevOne:
The syntax is server IP address (SNMP target)@port (161 UDP by default),/SNMP community name (normally is public), in my case I have two target servers for SNMP, you can configure more than one using “comma” to separate.
esxcli system snmp set --targets=192.168.0.5@161/public,192.168.0.6@161/public
Then type enable to enable SNMP services on those ESXi hosts:
esxcli system snmp set --enable true
Restart the SNMP service using:
/etc/init.d/snmpd restart
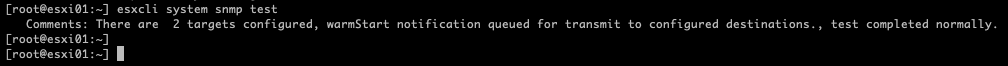
You can also test the SNMP sending traps to SevOne using:
esxcli system snmp test
Now, let’s configure SNMP on vCenter, the process is very similar:
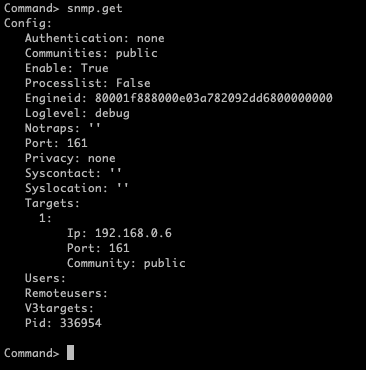
Connect through SSH to vCenter and type snmp.get (in my case everything is configured)
First of all, configure the community name, in my case is “public”
snmp.set --communities public
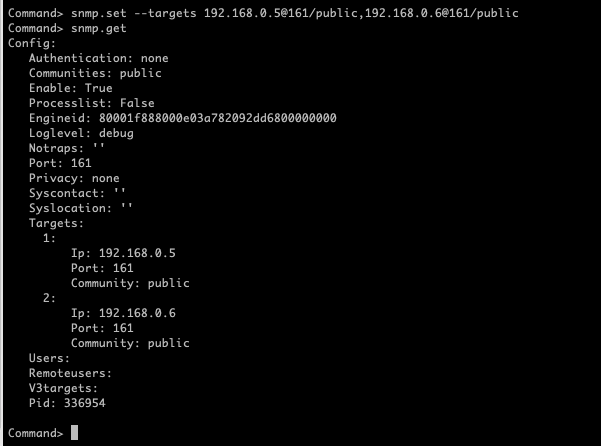
Configure the target using the following command, to separate targets use a comma:
snmp.set --targets 192.168.0.6@161/public(example of one targer)snmp.set --targets 192.168.0.6@161/public,192.168.0.5@161/public(example of multiple targets)
You can also set the SNMP log level using below command:
snmp.set --loglevel <DEBUG|INFO|WARNING|ERROR>
Then, enable SNMP:
snmp.enable
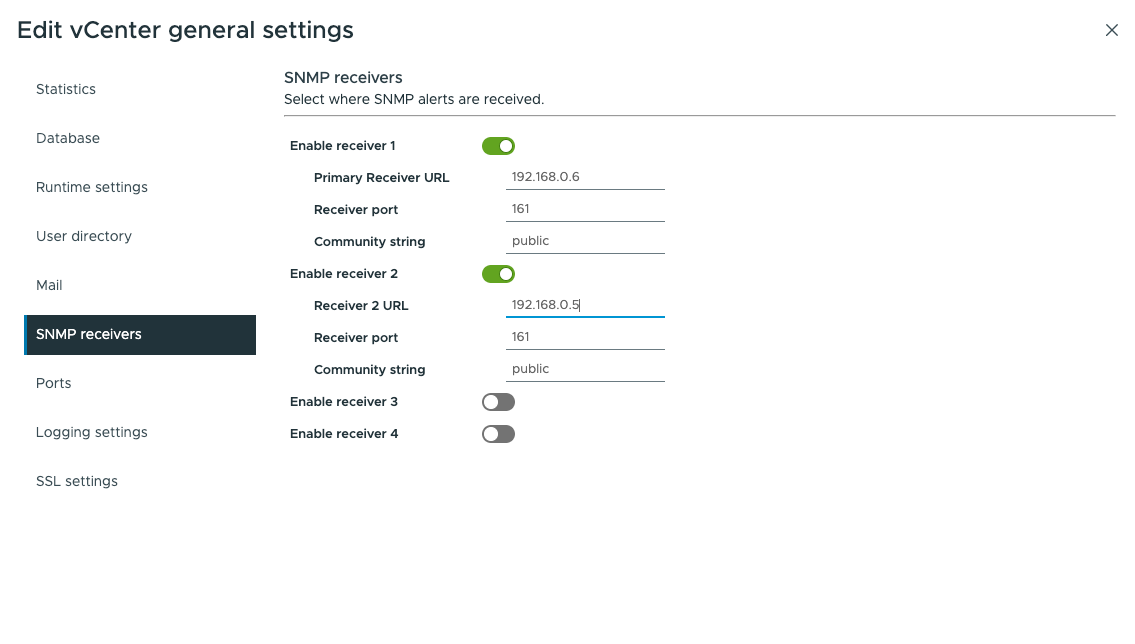
At this point the vCenter can send SNMP information about status to the receivers, but, for another kind of information you also need to configure this information on vCenter GUI interface, following:
Click on vCenter > Configure > General > Edit > SNMP section
then:
Ok, right now let’s configure the vSphere as a sender on SevOne NMS appliance, log in on it with GUI interface:
There are two ways to configure that, let’s do to in the easiest way (I think !!!!)
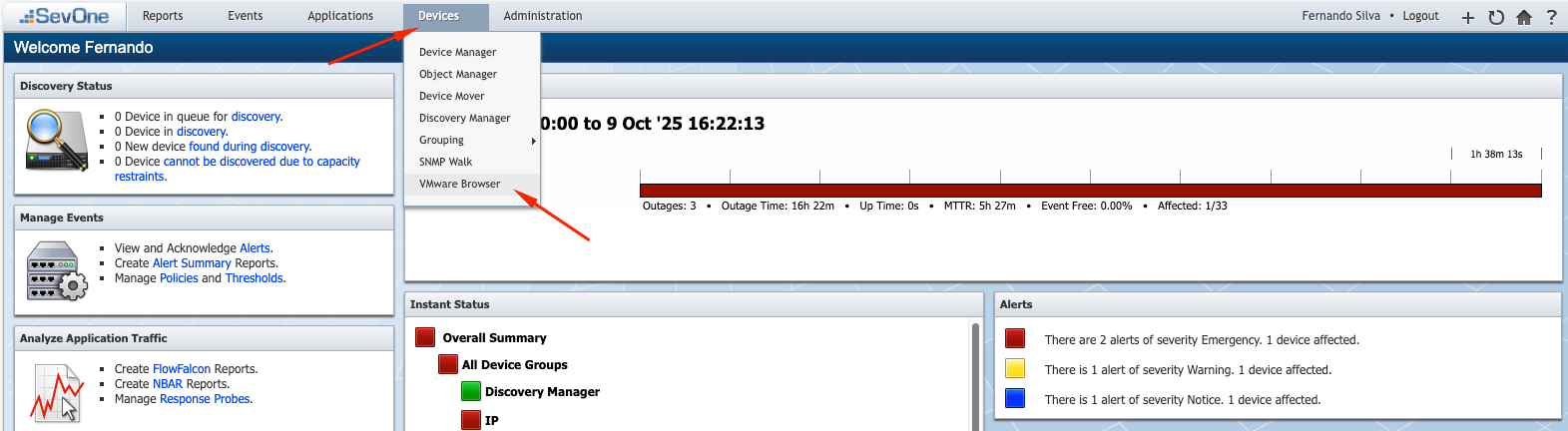
Click on Devices > VMware Browser
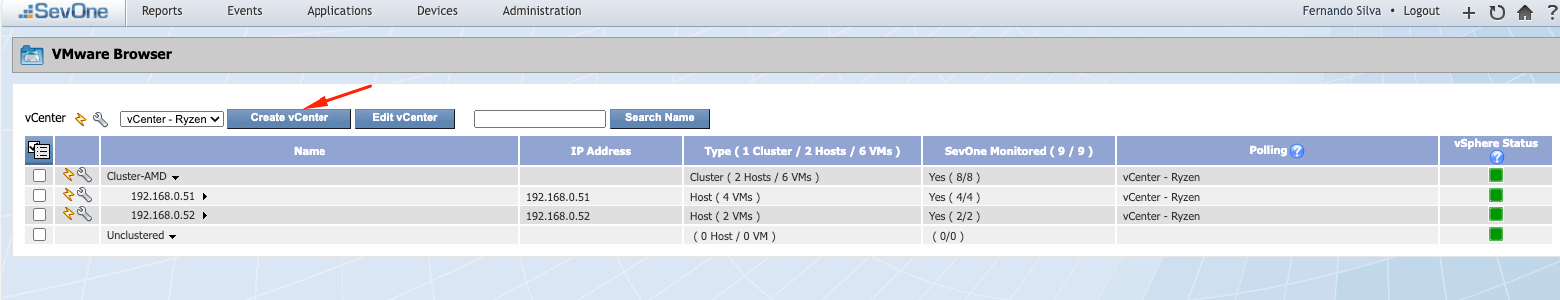
Then, click on “Create vCenter”, in my case I have already configured it previously:
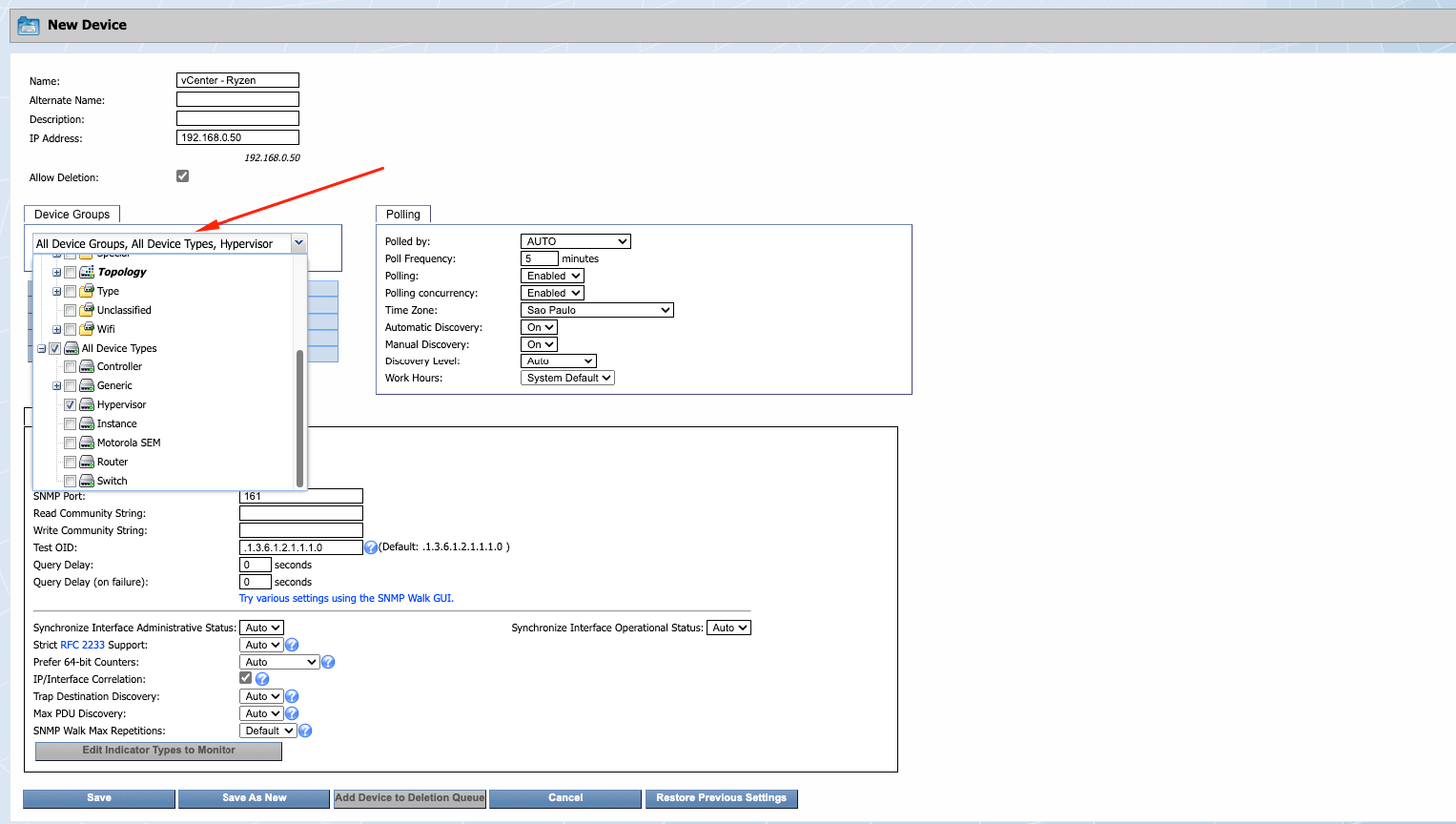
Fill in the requested information:
Choose the Device group as you want, it is just to organize the devices in categories , we will use those groups in rules, reports etc in future post:
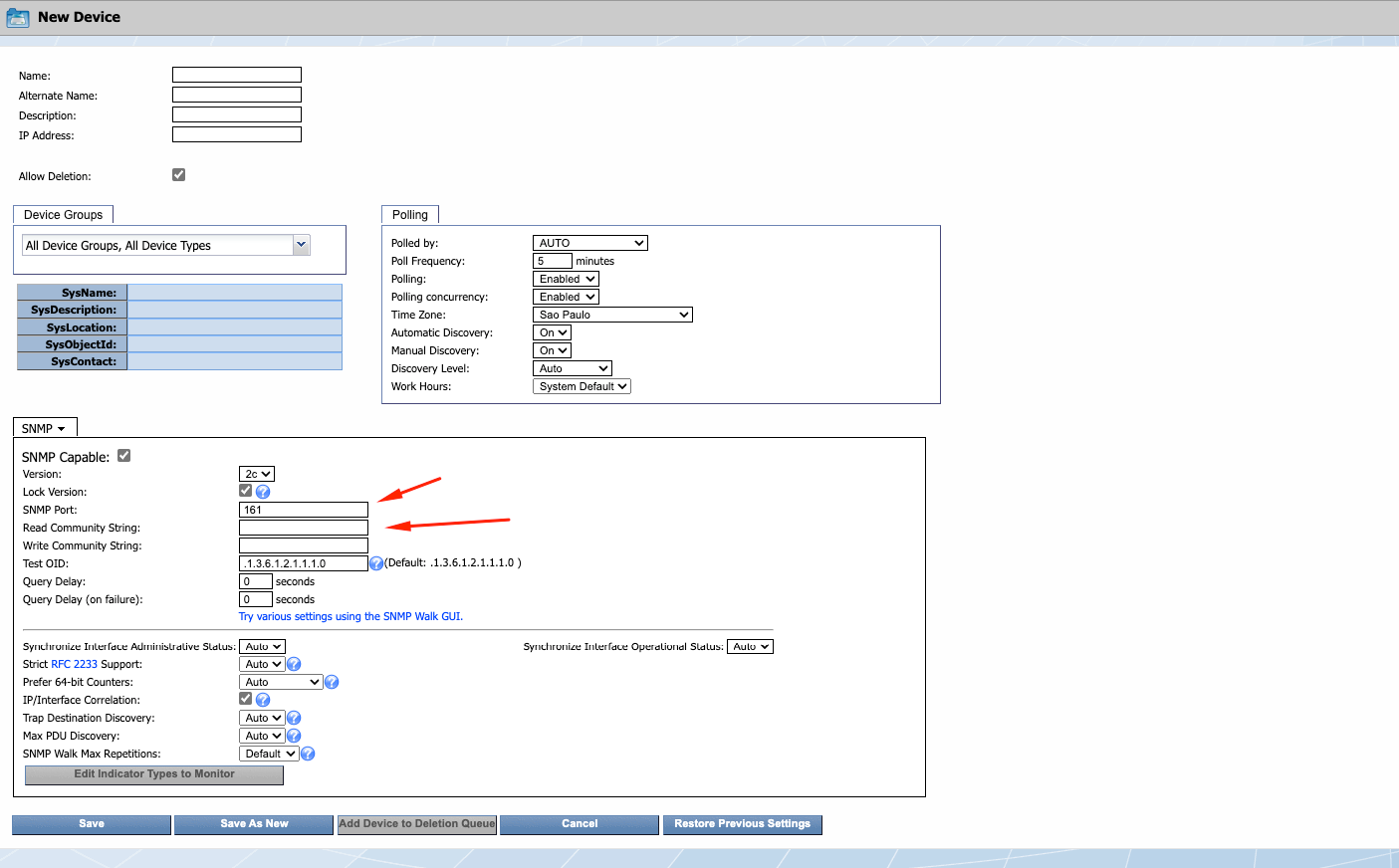
Also, fill in the information about SNMP previously configured on vCenter and hosts ESX’i:
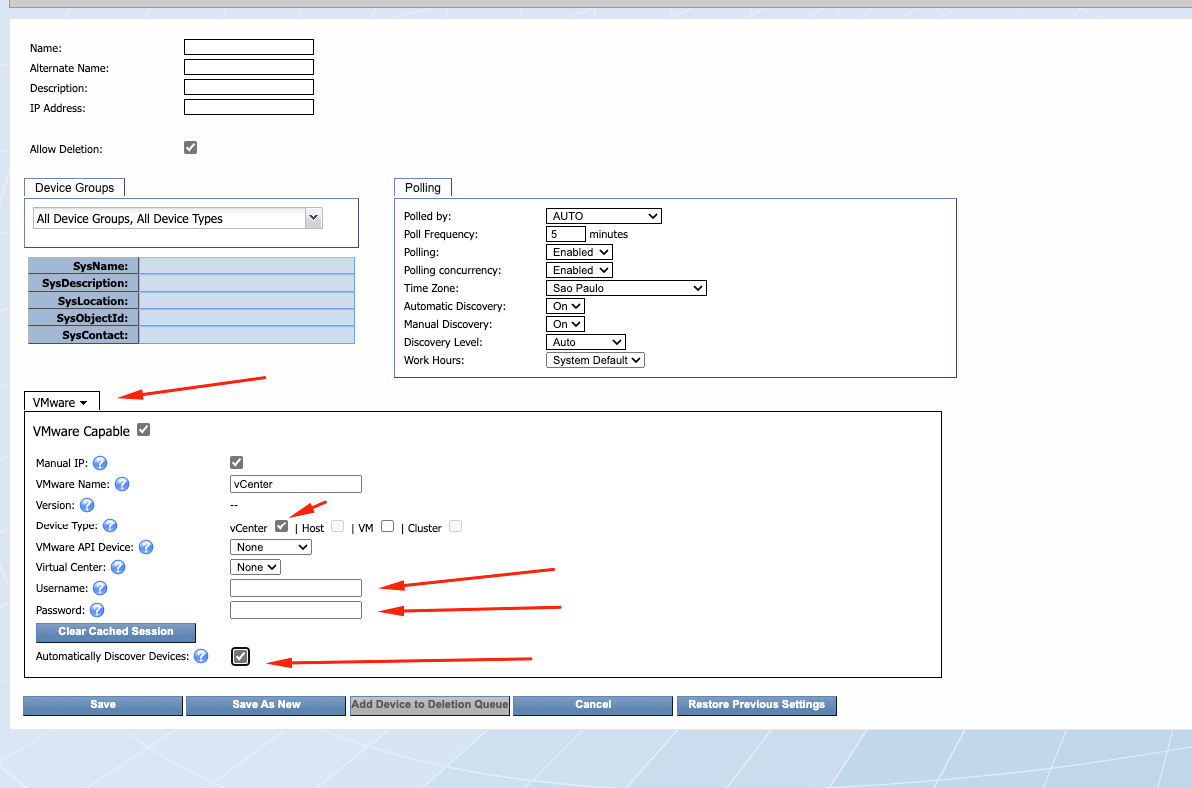
Choose the SNMP tab to VMware and fill in the login information, enabling SevOne to automatically discover devices inside the vSphere environment, like ESX’i hosts and VM’s:
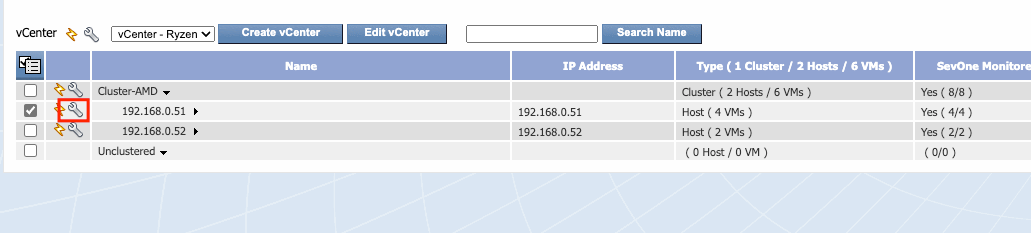
After that, click on “SAVE” and wait SevOne to connect and discover the necessary information, also start receiving SNMP traps.
After the SevOne discovery, the hosts ESXi and VM’s, click on each host and make sure that the SNMP configuration is the same as configured previously.
Ok, so right now lets to configure NetFlow on virtual switches to receive the information about flows that are crossing our network.
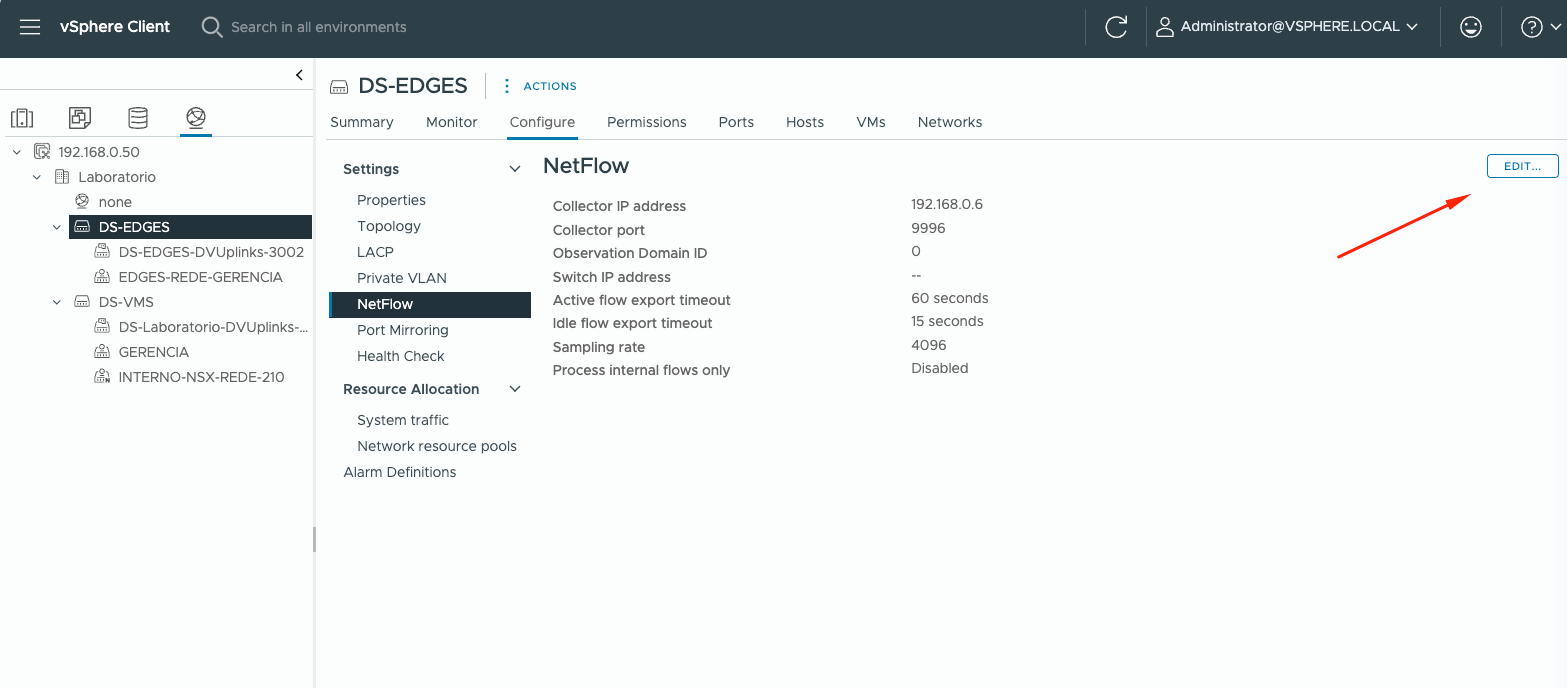
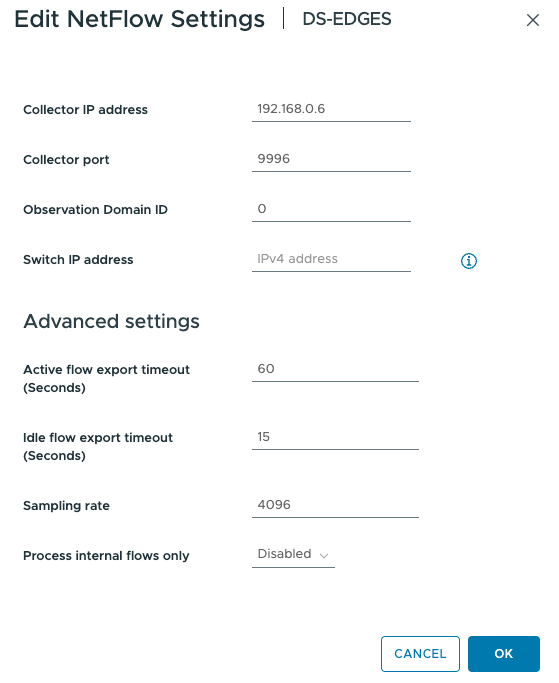
Go back to vCenter Gui interface and click on Network > click on each VDS > Configure > Netflow > Edit
Fill in the information of SevOne IP address server, the default port of SevOne is 9996
Configure it to each VDS that you want to send Netflow.
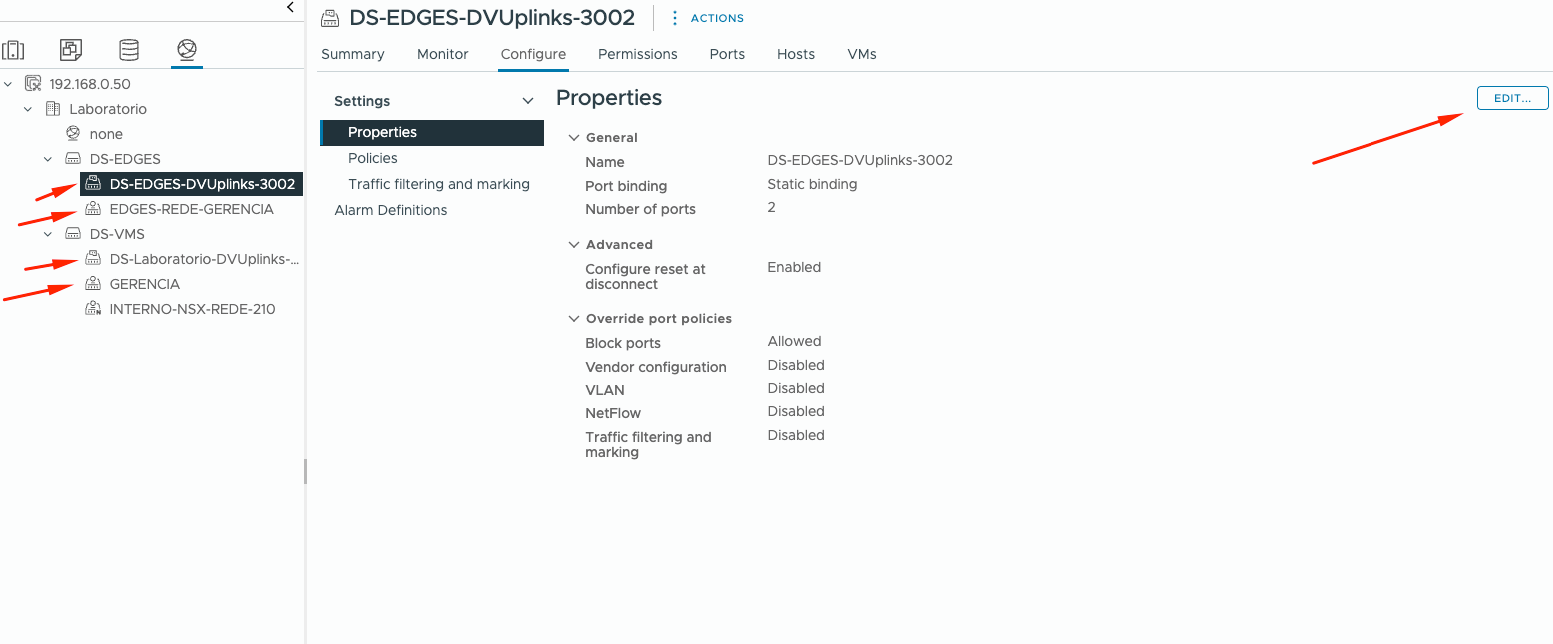
Also, enable Netflow on each Portgroup:
Click on each PortGroup > Configure > Properties > Edit
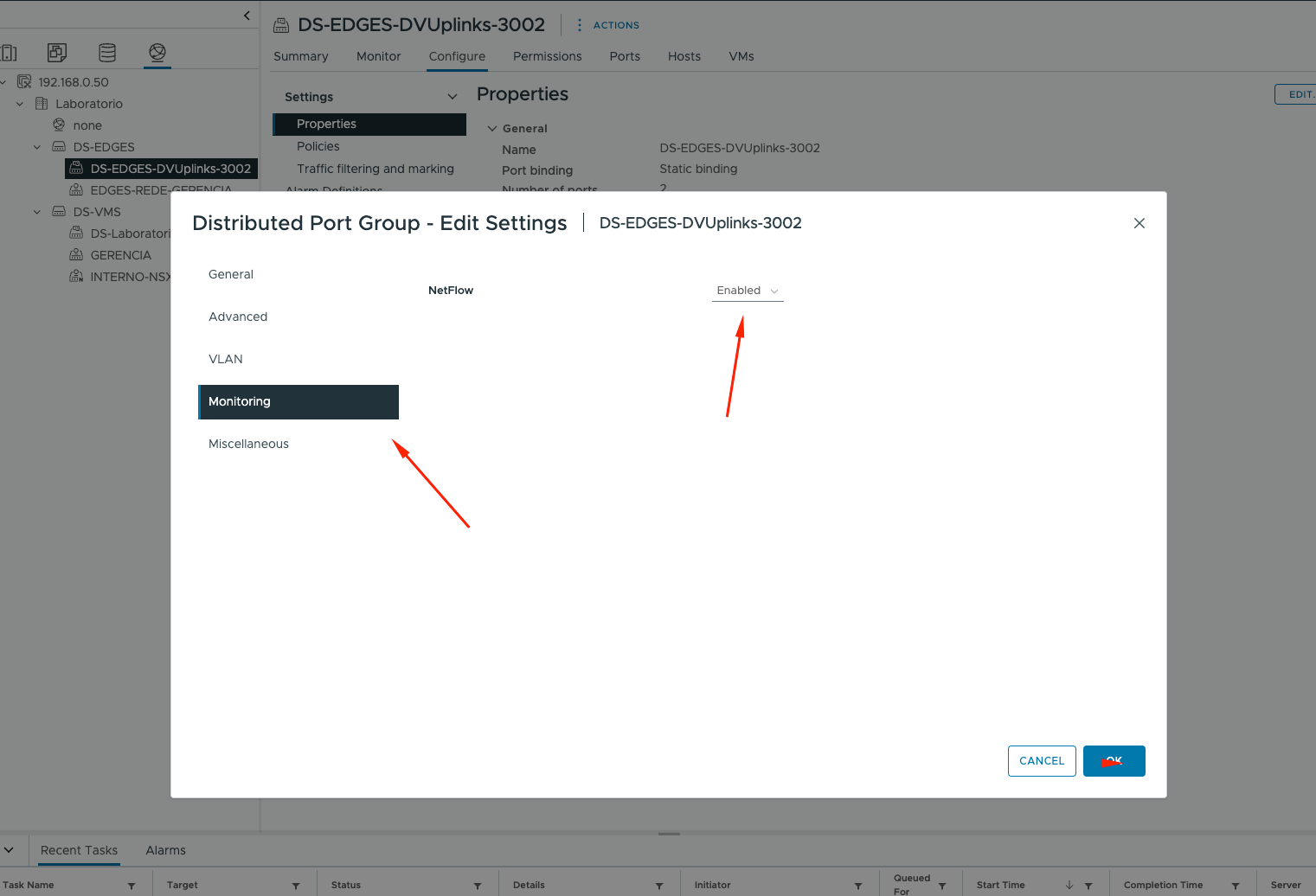
And then go to Monitoring and enable Netflow:
Enable NetFlow in each portgroup, including the portgroup used as Uplink Portgroup, of course, enable just on Portgroups that you want to receive Netflow information on SevOne.
Go back to SevOne Appliance just to make sure that you have rules enabling to receive all packets of Netflow sent by VMware.
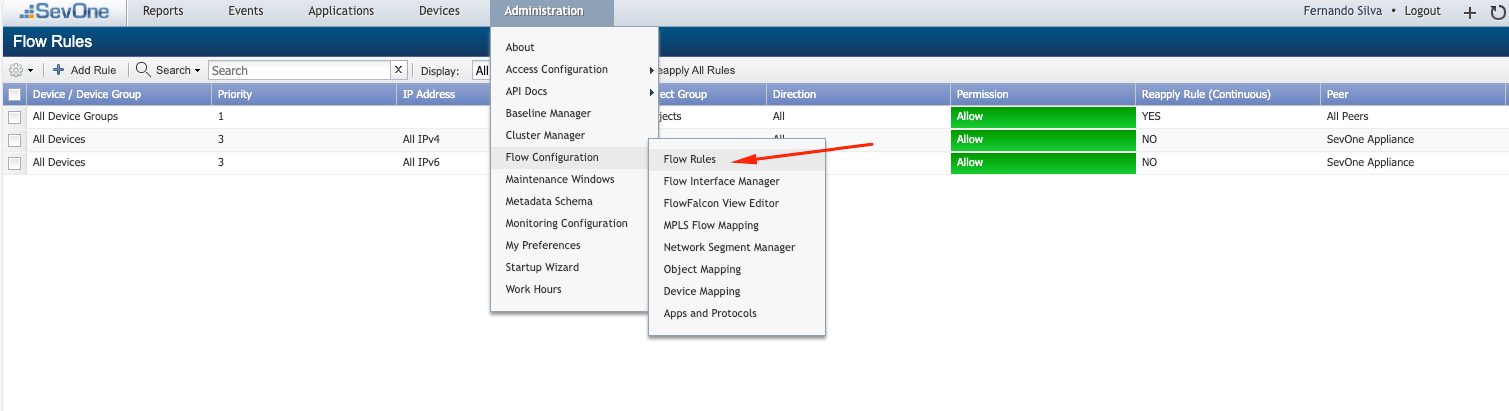
Go to Administration > Flow Configuration > Flow Rules
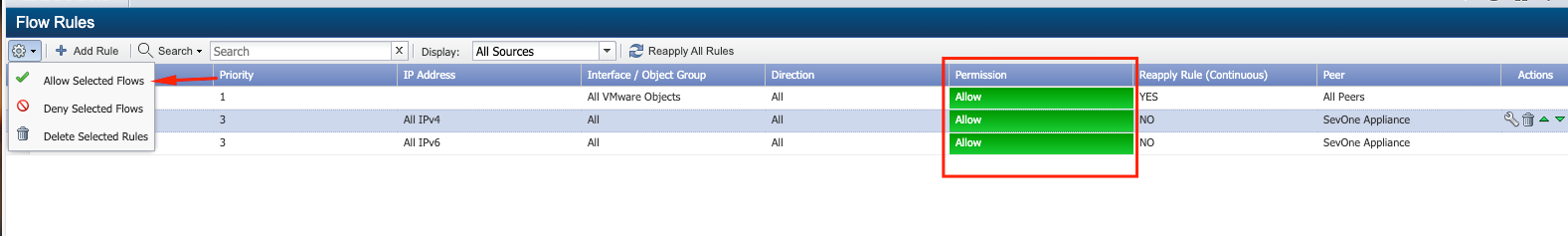
Make sure that you have rules allowing VMware devices to send information to SevOne, those rules are used to manage the information that is received by SevOne, blocking for example that SevOne receives information from LAN interfaces of some device, but allowing it from the WAN, they are just rules to restrict what information you want to receive, in my case I kept the default rule, allowing everything, I just enabled it.
Ok, lets to test if everything is ok!!!
Go to the SevOne Data Insight appliance, this appliance transforms network data received by SevOne NMS Appliance into actionable insights to optimize IT operations, enabling the creation and sharing of reports and workflows with the SevOne Network Management System (NMS)
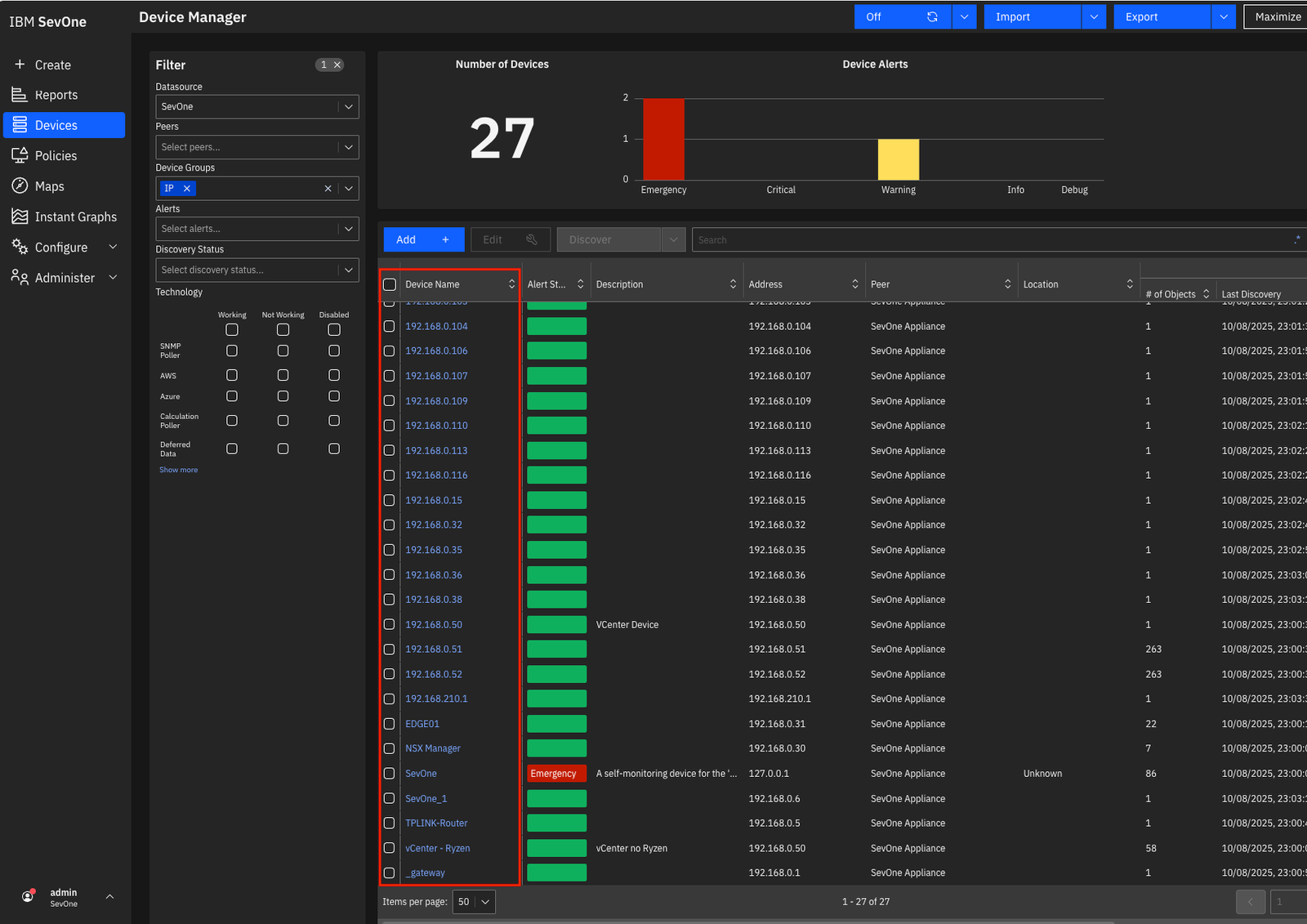
Log in to the appliance and go to Device in the menu:
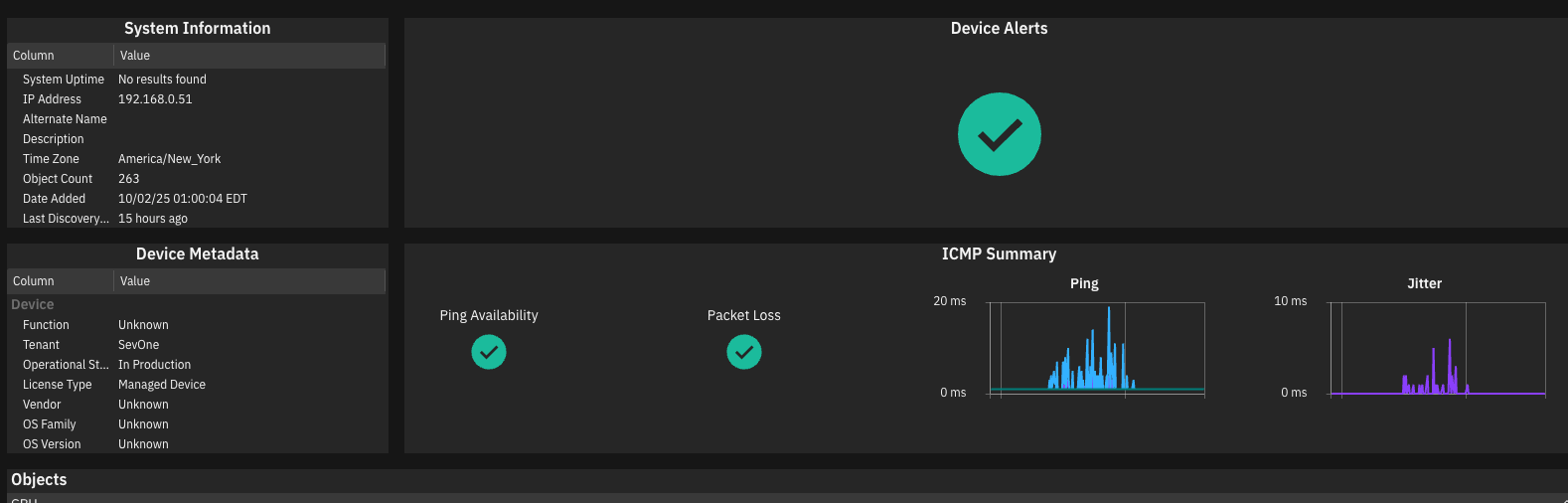
In my case, as I configured the SevOne to discover the VM’s using vsphere credentials, I already have some devices configured automatically.
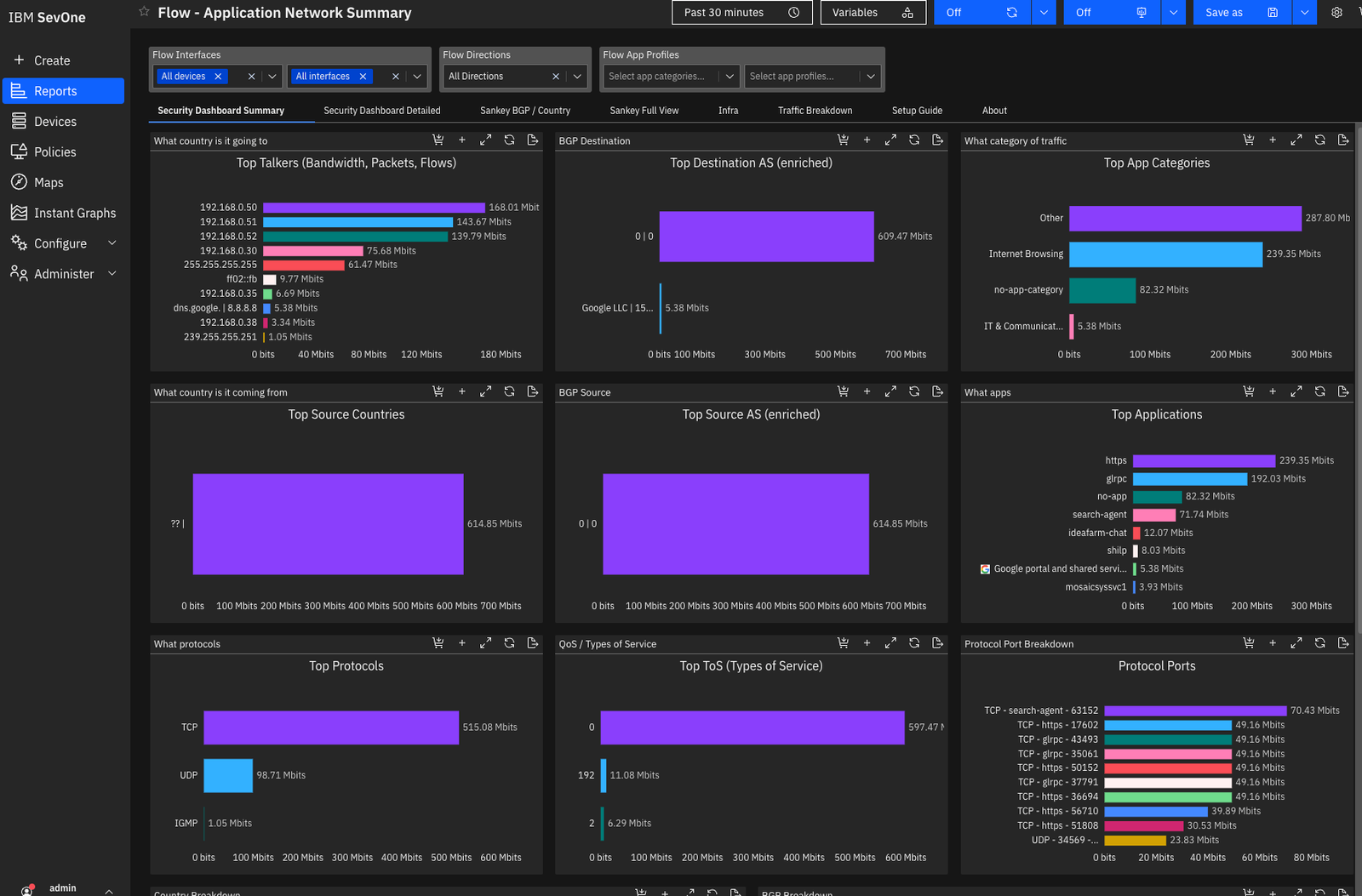
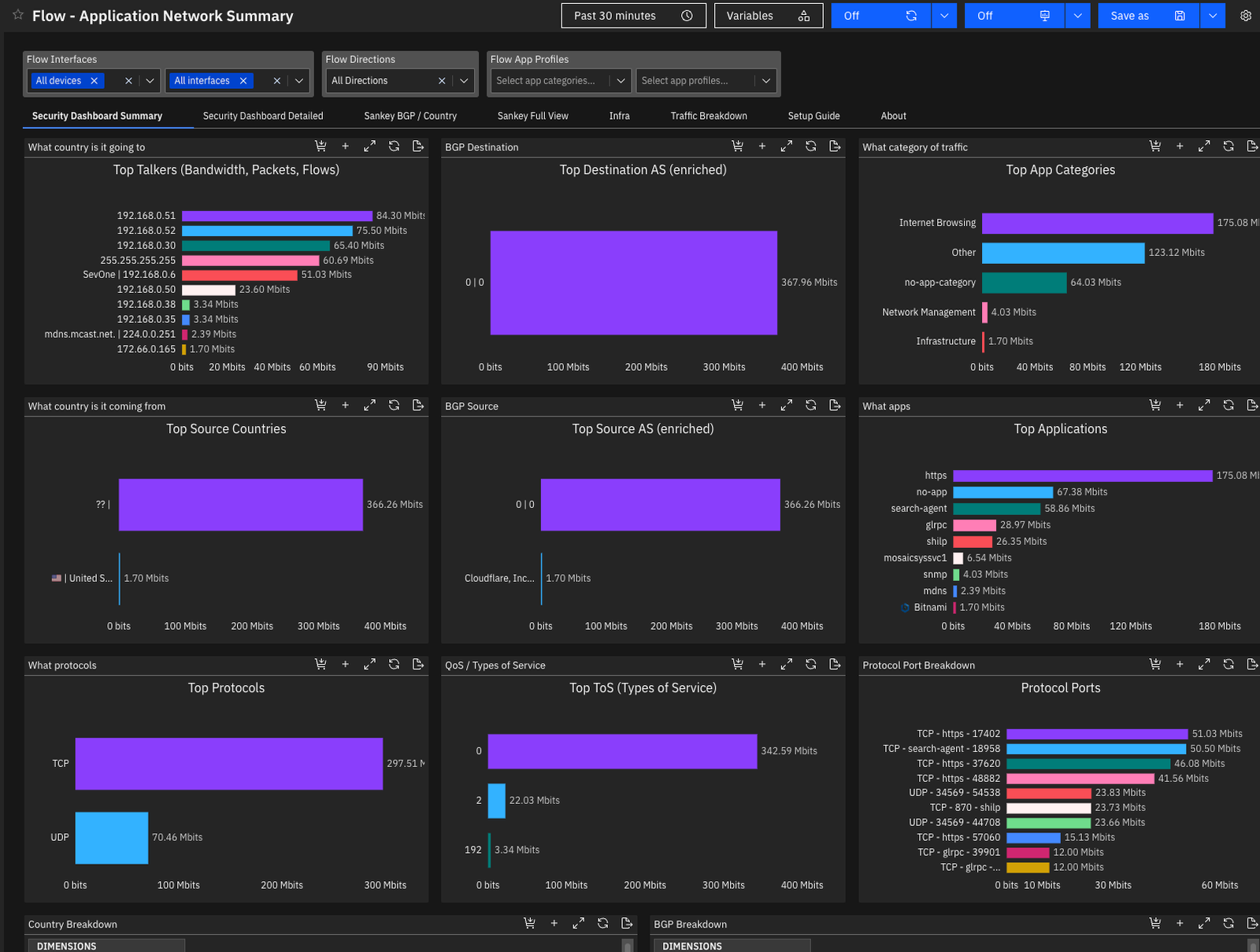
Let’s check some Reports, click on Reports on the menu and choose a ready report, for example Flow – Application Network Summary (remembering, I will cover how to create reports, Policies, maps etc in future posts).
And then choose in the source All devices and All interfaces:
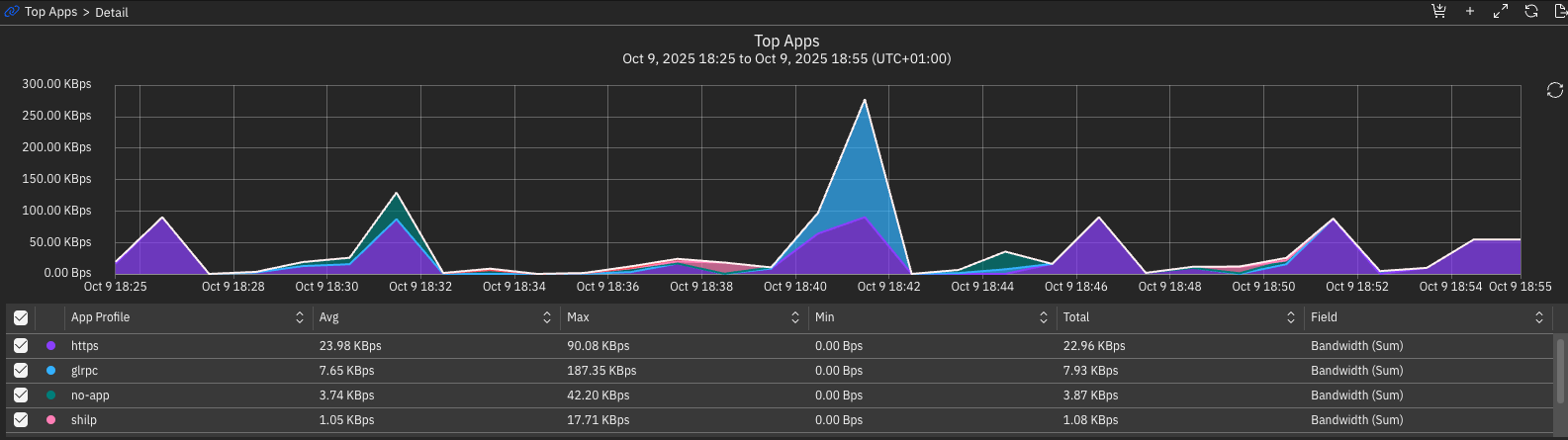
And voilà, now we are receiving information about flows, apps, IPs, devices and everything that travels on the network, in my case, I am using my homelab with a few VMs connected and at the time I am writing this post I had just discovered the devices, so I will still have little information.
In the next posts, we’ll talk about configuring IPFIX (NetFlow) on VMware NSX, configuring SDWAN devices like Fortinet on SevOne, etc.
See you next time!